Due to security requirement, most companies don’t allow Google Cloud SQL (Postgresql) to be accessible via public IP. This article shows how to configure private IP for the db so that a web service built on App engine can communicate with the db.
Step 1. Configure Cloud SQL to use “Private IP” and specify its associated network. Note down the assigned private IP as this will be used later.
Step 2. Create a “Serviceless VPC access” connector in “networks”. Make sure the same VPC network used in step 1 is used and use Custom IP range in subnetwork section. The custom IP range should be in the same network of the DB’s private IP. For example if the DB’s private IP in step 1 is 10.217.32.3, subnet should be something like 10.217.0.0/28.
Also make sure this connector is in the same project, same region of the App engine.
Step 3. Modification of the App engine app:
a. in app.yaml, add a line like like the below
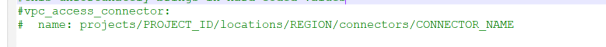
b. in the code, the connection url is changed to
DATABASE_URL=’postgresql://’ + DB_USER + ‘:’ + DB_PASS + ‘@DB_PRIVATE_IP:5432’ + ‘/’ + DB_NAME
from
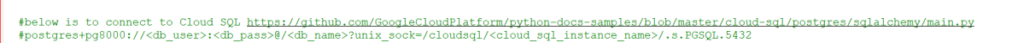
Reference Google doc: https://cloud.google.com/sql/docs/postgres/configure-private-services-access
